
Image taken from Ivan David Gómez's Flickr account under the Creative Commons license.
This article was written by Ramiro Rivera and was originally published in Spanish on the website Sin Embargo.
Last week's attack on the surveillance technology firm Hacking Team was not the ordinary information leak that hackers, “hacktivists”, and other online experts have grown accustomed to over the years. This time around, the ones left exposed were not only governments and institutions, but also a company that specializes in making the very tools that governments use to carry out espionage and surveillance.
This is not the first time Hacking Team has found itself at the center of controversy. The Milan-based firm carries a long list of accusations regarding unethical commercial actions and the selling of software to aid its clients (mainly governments) in violating telephone and computer security.
The attackers also hacked the company's official Twitter account and used this to point to the torrent file of more than 400 gigabytes of leaked internal data: Emails, bills, client lists, and even the company's product source code. The disclosure of this information comes right in the middle of a long, worldwide debate over how to control spy software.
Mexican human rights defender Jesús Robles Maloof, who has a key figure in spreading information about the hack in Mexico, described the leak as a huge surprise:
“Fue una sorpresa para todos que se haya filtrado y no usaran la plataformas convencionales. Lo hicieron de manera que también protegiera la fuente de la filtración.”
“The information leak and the use of non-conventional platforms was a surprise for everyone. They also did it in a way that masked the source of the hack.”
On his Twitter account, he published six purchasing receipts from Hacking Team with the company name SYM Servicio Integrales, which made various purchases from the company for between €319k and €925k (USD $350k and $1.02 million).
Until now, seeing the surveillance company's presence spread throughout the globe has not taken anyone by surprise. What is surprising are the details of the transactions, which include countries that previously have denied possessing these types of tools.
According to Wired Magazine, the US Federal Bureau of Investigation is one of the clients that has acquired software from the Italian company. This is by no means outside the realm of possibility. It has long been suspected that the FBI used software from Hacking Team, but since the publication of the leaked data, there is now hard evidence showing this to be true.
However, the FBI was not the only one left exposed. Since Sunday evening's leak, 14 major clients have been exposed, which besides the US include governments and institutions from Mexico, Ethiopia, Chile, Spain, Honduras, Sudan, and Panama to name a few.
Luis Fernando García (@tumbolian), director of the Red en Defensa de los Derechos Digitales (Digital Rights Defense Network), or R3D told Sin Embargo:
“Son más de 400 gigabytes de información, por lo que se va tomar un tiempo acceder a toda y poder analizarla, así como las implicaciones que tiene. Sin embargo, de lo que ya hemos logrado acceder y conocer, que es relevante, pues es precisamente la lista de clientes de Hacking Team, que en México es bastante amplia. Es el país que tiene más clientes… Y que incluye tanto a autoridades federales como estatales.”
There are more than 400GB of information, therefore, it is going to take some time to access and analyze all of the data, including its implications. However, from the relevant information that we have already accessed and identified, Hacking Team's client list from Mexico is quite long. It is the country that has the most clients…and it includes federal authorities as well as authorities at the state level.
In Mexico, the clients’ leaked information appears on this list:
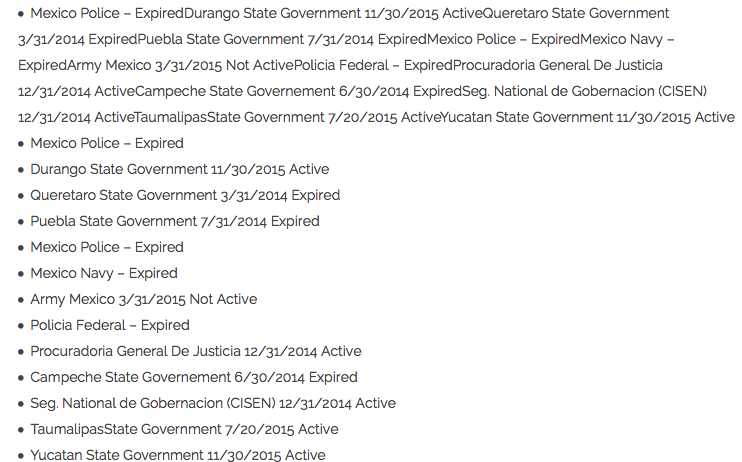
List of Mexican institutions that were or are Hacking Team's clients.
In the list of buyers, some appear to be “active”, or current clients of Hacking Team; for those labeled as “expired” or “not active”, contracts have presumably been terminated.
All of this information places authorities in a difficult situation. First, given that several institutions not belonging to law enforcement appear on the list, some suspect that these activities are therefore illegal because these institutions do not have the “constitutional powers to carry out investigations.” There would be “many questions they would have to answer to” given the software's invasive nature, García adds.
The issue of cost is also important and in need of clarification. “The issue of contracts, prices, procurement methods…They are large sums. […] It appears there was a price increase…The ties [linking] intermediary companies [to governments and institutions] need to be looked at,” he says.
El @gobqro compró a Hacking Team a través de intermediario Teva Tech de México S.A. de C.V. pic.twitter.com/6RK92GAVsN
— Compa Tumbo (@tumbolian) July 6, 2015
The @gobqro (government of Querétaro) bought Hacking Team through an intermediary company, Teva Tech of Mexico.
Una de las muchas facturas del CISEN y Hacking Team. Esta por 200,000 ¿Euros? pic.twitter.com/mv3Foy0XvW
— Compa Tumbo (@tumbolian) July 6, 2015
One of the many purchasing receipts of CISEN (Center for Research and National Security) and Hacking Team. It's for 200,000…euros?
“If it is confirmed that authorities who do not hold surveillance powers…have purchased the software, well there could be very serious legal repercussions, including criminal punishment for authorities that have purchased these services,” adds García.
Surveillance State
“We could be looking at a country that is acquiring the best technological resources without there being any controls, and I believe that this can lead us to a surveillance state; a country that leans towards control,” says Robles Maloof.
“Technology and procedure that are not subject to citizen control is an authoritarian practice,” he adds. “Not only has the [software's] correct usage or positive impact not been shown, but rather —on the contrary— it has shown to be used strictly on the basis of secret criterion and that only a few people control it.”
Two years ago, the non-governmental organization Reporters Without Borders published a list of “Corporate Enemies of the Internet”, which apart from Hacking Team, included Gamma, Trovicor, Amesys, and Blue Coat. Under the NGO's rubric, the products of these companies “were or are used by the authorities of repressive countries in order to violate human rights and the freedom of information.”
For example, these companies’ surveillance and interception products allowed the Bahrain royal family to spy on and detain holders of information; gave the Syrian regime the chance to spy on dissidents and Internet users from around the country —as well as carry out arrests and acts of torture; and permitted Mohammar Qaddafi's secret police to obtain the passwords of journalists and digital activists.
The R3D director asserts that of the 400GB collected, there is unlikely to be any information that specifically references governmental and institutional targets at the moment of seeking out Hacking Team's services. Although there have been “clues and allegations”, it has not been confirmed that the surveillance software was used against adversary politicians or journalists. “It cannot yet be proven with certainty who the targets are,” he says. “It would have to be the object of a very thorough investigation.”
However, there is a call for “a wide accountability process”, says Robles Maloof.
“El proceso de rendición de cuentas es nulo y eso es preocupante. […] No puedes mentir en una democracia, no puedes mentir por tanto tiempo… Y es lo que el gobierno mexicano ha hecho sistemáticamente en todo esto que le llama ‘Guerra contra el narcotráfico’ bajo el pretexto de que no quiere que los grupos criminales conozcan esta tecnología, lo cual es mentira”, agrega.
The accountability process is null, and that's worrisome. […] You can't lie to a democracy; you can't lie for that long…And that is what the Mexican government has systematically done under what they call “the war on drug trafficking” and using this as a pretext to not wanting criminal groups to be aware of this technology, which of course is a lie.
[…]
We are barely into the first hours of the leak…We have to perform an analysis and verification study of this information. Independently we have to verify the content's information. It is very important to have this perspective.
According to the activist, the source of the hack remains unclear. What is known is that since 2012, Hacking Team officials have been present in Mexico. “We know that Hacking Team has an extended list of clients and now we have evidence…that dozens of government bodies in Mexico have acquired that software,” he says.




12 comments